Traffic access rules: Stop bots with precise segmentation & targeted mitigation

Every major website faces bots and the problems they bring with them. But everyone’s bot problem is unique. No other website has the same bots, the same vulnerabilities, the same threats as yours. No other company has your product range, sales delivery methods, and brand reputation. Traffic Access Rules lets you tailor your bots and abuse mitigation strategy to your specific needs and use case. It lets you level-up your bot protection with more control and customization of traffic than ever before.
Over 30% of all online traffic is bad bots. But what this number is made up of—and indeed the number itself—varies dramatically across regions, industries, and individual websites.
There’s no one-size-fits-all approach to bots and traffic management. There’s no switch every company can simply flick to create the perfect, most profitable, most accurate, flow of “good” traffic.
Some companies, for example, want scraper bots to pull data from their site to increase the volume and quality of referral traffic from third-party sites. Others want to keep scrapers off their sites entirely.
Some companies ship products internationally and expect traffic from across the globe. While for others, traffic from unfamiliar geographies represents trouble.
Some organizations need their support teams to be able to bypass their waiting rooms to access events. For others, this would be a threat to fairness and security.
There isn’t a one-size-fits-all approach to bots and traffic management.
Queue-it’s new feature, Traffic Access Rules, makes it easy to identify a segment of visitors and choose whether they should be challenged, blocked, or allowed to bypass the queue. It gives you more control and customization than ever before, so you can tailor your bots and abuse protection to your needs.
You can identify a segment of visitors based on:
- Static network analysis, like IP address or user agent
- User behavior, like reputation score
You can then configure access rules to:
- Challenge traffic you believe is suspicious
- Hard block traffic you know is malicious
- Allow specific traffic (such as support staff) to bypass the queue
These rules can be applied globally to all waiting rooms, to specific waiting rooms, or to different inflow types (scheduled or 24/7 protection).
Traffic Access Rules joins Queue-it’s advanced suite of bot mitigation and traffic control features, adding more flexibility, control, and customizability to how you handle traffic. It enables you to tailor your traffic management to your region, industry, business, use case, or business objectives.
RELATED: See More, Act Smarter: Your Bots & Abuse Situation is More Transparent Than Ever
A robust bot prevention strategy involves four stages: detection, assessment, mitigation, and evaluation. These four stages occur in a cycle, where in each stage you refine and iterate on your strategy.
Traffic Access Rules fits into the “mitigation” stage of bot prevention. And mitigation works best when you have the data to detect, assess, and evaluate your past, current, and future events—which can be found in Traffic Insights.
Traffic Insights is where you get the information you need to act; Traffic Access Rules is where you put those insights to work.
You can use the detailed dashboards and analytics from Traffic Insights to identify the threats and traffic patterns specific to you, then configure access rules accordingly.
Examples of Traffic Access Rules based on Traffic Insights
|
Detect with Traffic Insights |
|
Mitigate with Traffic Access Rules |
|
Aggressive IP address |
|
Challenge those IP addresses |
|
Data center traffic |
|
Block data center traffic |
|
Unexpected user agent |
|
Challenge traffic with that user agent |
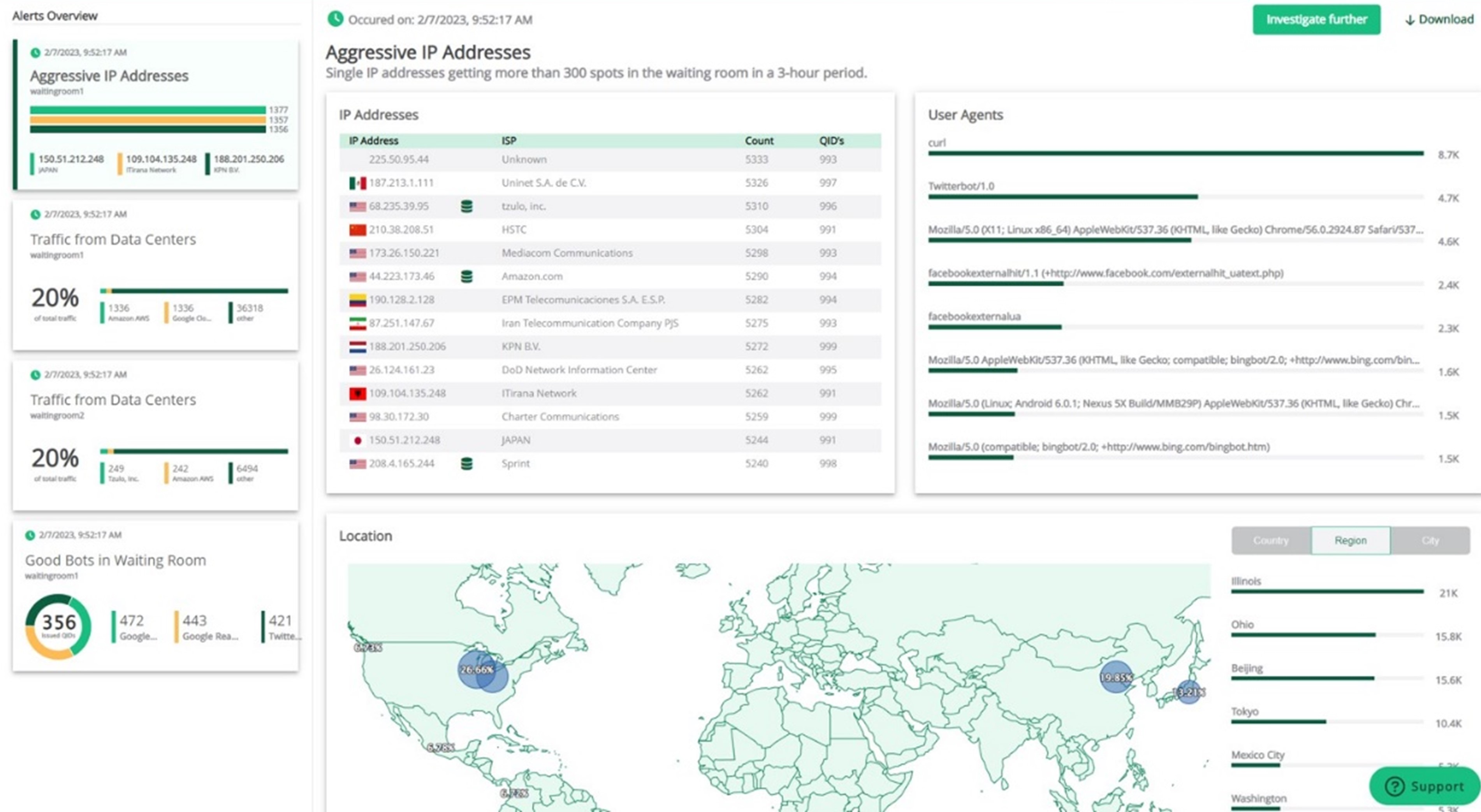
The Traffic Insights Alerts dashboard in the GO Queue-it Platform showing aggressive IP addresses, data center traffic, user agents, and more
To use Traffic Access Rules, you’ll need to have the Bots & Abuse feature on your Queue-it subscription.
Traffic Access Rules works by triggering an action based on a set of conditions, like an IF-THEN statement. For example:
- IF [reputation score=high risk], THEN [Challenge traffic]
- IF [IP address=your company IP address], THEN [Bypass queue]
- IF [Classifier=Queue-it Datacenter], THEN [Hard block traffic]
The IF conditions are where you choose the type of traffic you want to act on. You can choose one IF condition, or stack multiple together using “ANY” or “ALL” logic. The THEN actions describe how to respond to that traffic.
Traffic access conditions
Examples of IF conditions that give you a high degree of control in identifying your target visitors are shown in the table below.
|
Condition |
Description |
Example |
|
ASN |
The ASN (Autonomous System Number), a range of IP addresses controlled by a specific identity (e.g. ISP (Internet Service Provider) or Governments) |
Block traffic coming from ASNs known to be the source of malicious traffic |
|
Classifier |
A pre-existing data set maintained by Queue-it (e.g. data center traffic) |
Challenge traffic coming from data centers |
|
HTTP Header |
Information that comes with visitor page requests and can contain parameters like referral source or browser language |
Challenge traffic from visitors with a browser language outside your target market |
|
IP Address |
The address identifying a specific computer or computer network |
Hard block aggressive IP addresses |
|
IP Range |
A subnet of IP addresses |
Allow staff from your company IP address to bypass the queue |
|
Reputation Score |
A dynamic Queue-it-assigned score of how trustworthy a visitor is (0 is lowest, 100 is highest) based on user behavior and additional data |
Challenge traffic with an average reputation score for extra security |
|
User Agent |
Metadata that accompanies visitor requests |
Challenge visitors using outdated browser versions |
|
Waiting Room ID |
ID of a specific waiting room used to narrowly apply your traffic access rules |
Challenge certain traffic in one waiting room but block certain traffic in another |
|
Waiting Room State |
State of a waiting room used to narrowly apply your traffic access rules |
Block traffic when the waiting room is in 24/7 protection mode |
Traffic access actions
Examples of THEN actions that give you flexibility in how to act on your identified visitors target visitors are shown in the table below.
|
Action |
Description |
Example |
|
Bypass waiting room |
Allow user segment to bypass the waiting room for immediate access to your website or webpage |
You want support staff from your organization to have direct access to troubleshoot issues on your site |
|
Challenge |
Challenge the user segment with a Queue-it CAPTCHA |
You want to determine if traffic from an IP address range is genuine or malicious |
|
Hard Block |
Deny access to the waiting room |
You want data center traffic to be denied access to your sale |
To create a traffic access rule, visit the GO Queue-it Platform and select “Traffic Rules” then “Setup” in the left-hand column.
From the Traffic Rules page, add a new rule by clicking the “ADD RULE” button in the top right corner.
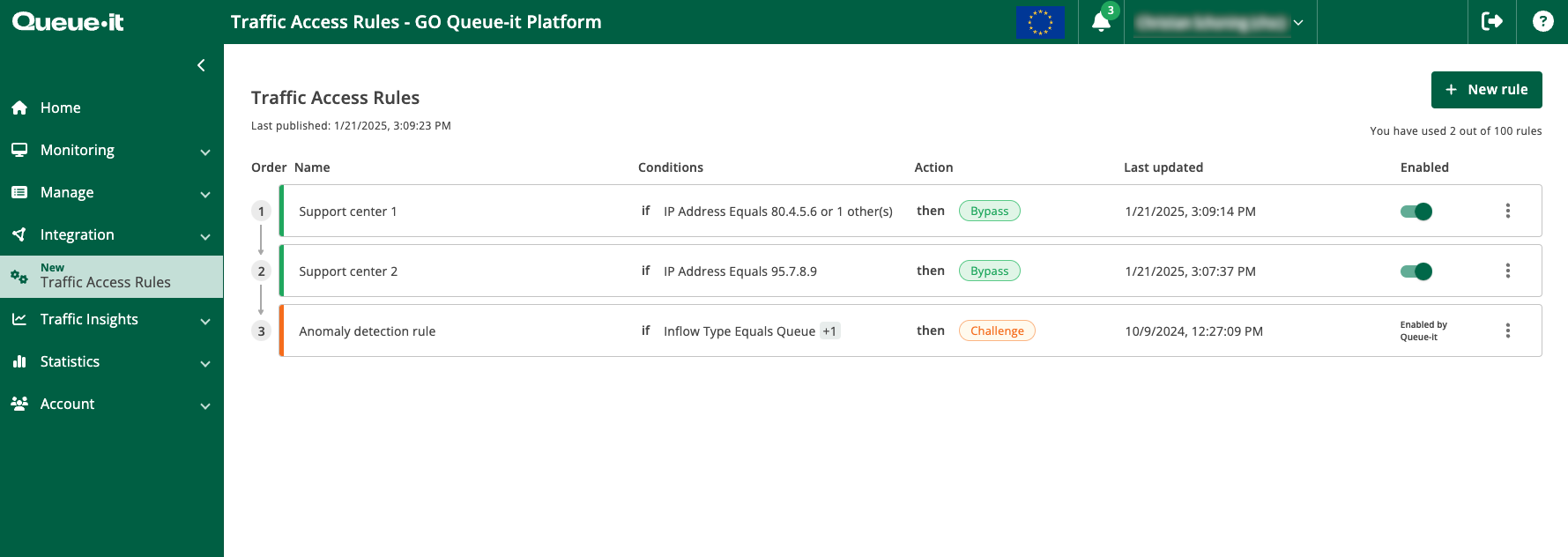
From the create rule page, you can add a name to your rule to describe its function, then create the IF-THEN criteria for the rule using the drop-down menus and free text forms. Click “SAVE RULE” when you’re done.
Traffic Access Rules joins Queue-it’s advanced suite of bot mitigation and traffic control features, adding more flexibility, control, and customizability to how you manage your traffic.
To customize your bots and abuse protection to suit your needs, you can configure access rules to:
- Challenge traffic you believe is suspicious
- Hard block traffic you know is malicious
- Allow specific traffic (such as support staff) to bypass the queue
This helps you improve the sale or registration experience, both for staff and customers.
Traffic Access Rules gives you the power to act on the detailed analytics and data in the Traffic Insights Data. It lets you customize and optimize the “mitigation” stage in your bot protection strategy.
To use Traffic Access Rules, you’ll need to have the Bots & Abuse feature on your Queue-it subscription. If you’d like to strengthen your bots and abuse mitigation strategy and get access to Traffic Access Rules, contact your Customer Success representative.