Improve bot protection with new data center IP blocking
Traffic from data centers has a high probability of coming from bots or other malicious users. Queue-it’s Abuse and Bot Protection now includes the ability to identify and block suspicious traffic emanating from data centers.
Use Case
To arrive at your website, visitors typically connect to the internet from their home or workplace. However, sometimes your website traffic will emanate from data centers, which are buildings that house servers and other computing infrastructure. This traffic either:
- is created by bots or scripts executed from a server in the data center, or
- passes through the data center when users connect using a VPN.
Whether the traffic comes via a standard internet connection or a data center is evident from the IP address. Genuine users rarely originate from data center IP address ranges.
VPN connections are commonly used to mask user identity. In the context of virtual waiting rooms, visitors using a VPN are usually trying to gain an advantage such as obtaining multiple places in the waiting room by hiding their real IP address.
Traffic that originates in data centers frequently come from bots that are hosted there. Scalpers and other bad actors can purchase server space in a data center and easily obtain hundreds of IP addresses to obtain multiple places in the waiting room.
Analysis of traffic from data center IP addresses show distinct patterns that clearly indicate they are used by bots and for abuse. Queue-it data shows that 13% of total traffic to the virtual waiting room originates from data centers, even though data centers make up only 3% of all IP addresses. In some cases, data centers are responsible for over 40% of the traffic to individual waiting rooms.
Solution
To help you ensure fairness and serve genuine customers, Queue-it has given you the ability to challenge or hard-block traffic that emanates from a known data center. Queue-it works with trusted 3rd parties to obtain the list of data center IP addresses and keeps it continuously updated.
When you enable traffic challenging, visitors with a data center IP address will need to solve a CAPTCHA before entering the waiting room.
When you enable hard-blocking, visitors with a data center IP address will see a 403 forbidden HTTP error code and will be unable to enter the waiting room.
Remember, Queue-it’s Abuse and Bot Protection already includes Anomaly Detection that challenges suspicious traffic, like connections with very short latency and multiple requests from the same IP address. Data center blocking bolsters this existing Abuse and Bot Protection. For more information, read the Bots & Abuse Management white paper, available in the GO Queue-it Platform
How To
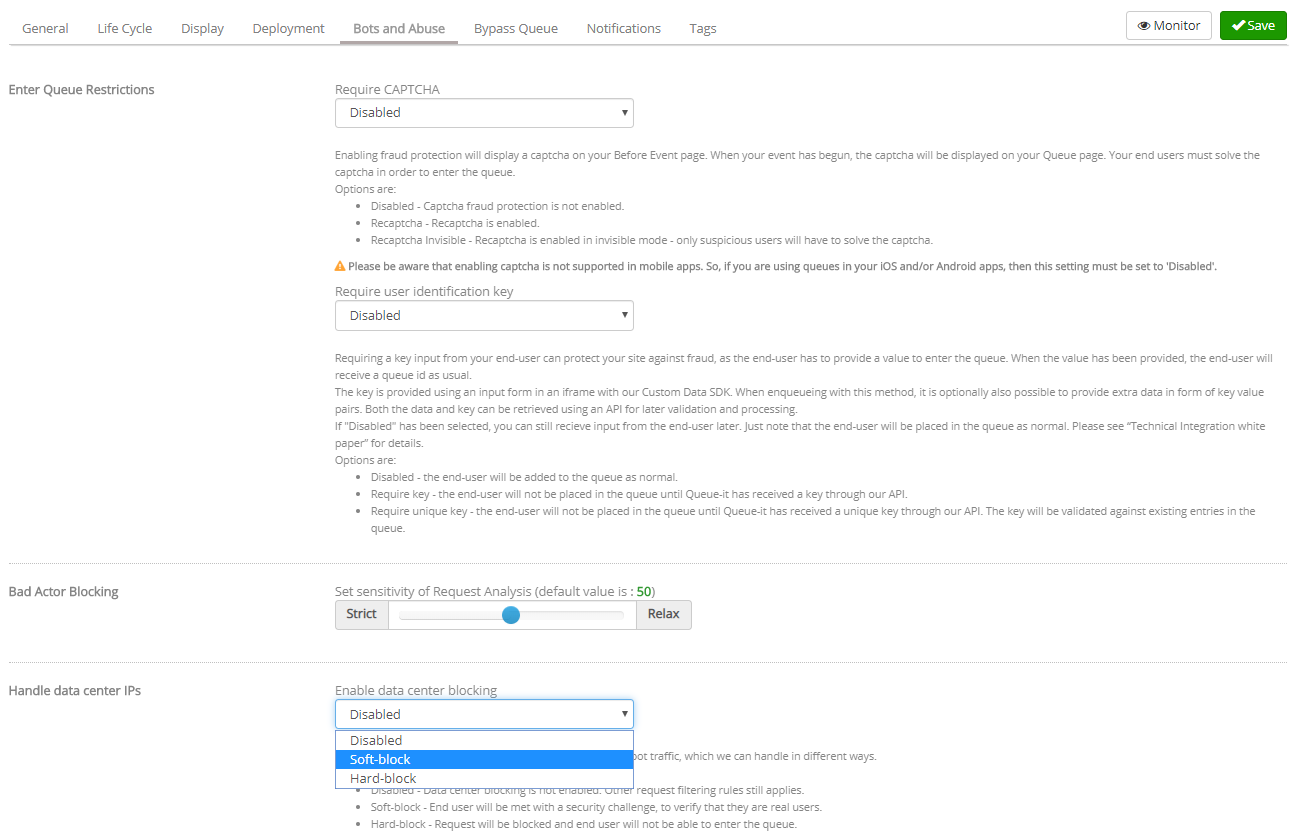
You can find the Data Center IP Blocking feature under the “Bots and Abuse” tab on event settings in the GO Queue-it Platform. If you are unable to locate the tab please contact your Queue-it support representative at support@queue-it.com. The Data Center IP Blocking feature is part of Queue-it’s Abuse and Bot Protection package.
To enable traffic challenging, change the setting to “Challenge.” To enable hard-blocking, change the setting to “Hard-block”.
Key Takeaway
Given the high volume of traffic from data center IP addresses, the new Data Center IP Blocking feature can be a valuable tool to improve waiting room fairness for your genuine visitors. Though not a silver bullet, the Bots and Abuse package contains several features that you can use to mitigate the types of bots and abuse you experience.
For more information on how you can tailor your bot and abuse protection to your needs, contact your Queue-it support representative at support@queue-it.com.